SELECT keyword in REXX is like switch case keyword used in c. This keyword allows to select one of the conditional expressions.
syntax :
select
when cond1 then …
when cond2 then …
otherwise …
end
example :
/*rexx*/
number = 100
select
when number < 5 then say "less than 5" /*condition not sastisfied.this statement will not get executed*/
when number < 50 then say "less than 50" /*condition not sastisfied.this statement will not get executed*/
otherwise say "it should be greater than 50" /*condition sastisfied.this statement will get executed*/
end
Saturday, November 29, 2008
Thursday, November 27, 2008
How to write a file in rexx
/*REXX*/
FILE = "N4C4F1.C3162.AUG13"
INPUT ="SAMPLE PROGRAM"
INPUT1 = "HOW TO WRITE a FILE"
INPUT2 = " THROUGH REXX"
DROP Z.
Z.1 = INPUT
Z.2 = INPUT1INPUT2
"ALLOC FI(OPDD) DA('"FILE"') SHR REUSE"
"EXECIO * DISKW OPDD (FINIS STEM Z."
FILE = "N4C4F1.C3162.AUG13"
INPUT ="SAMPLE PROGRAM"
INPUT1 = "HOW TO WRITE a FILE"
INPUT2 = " THROUGH REXX"
DROP Z.
Z.1 = INPUT
Z.2 = INPUT1INPUT2
"ALLOC FI(OPDD) DA('"FILE"') SHR REUSE"
"EXECIO * DISKW OPDD (FINIS STEM Z."
Labels:
Programming,
Technology
Tuesday, November 25, 2008
Pen Drive -a part of Life
Technology has always been a necessary evil.However, like many other equipments, pen drives are also a necessary evil and pose a potential security threat to the technology world. When placed in wrong hands, the portability and high storage capacity of the pen drive can be hazardous. The device has evolved as a threat to the corporate and other organizations where security of data is given utmost importance.
The threats that are associated with pen drives are serious. Some of them are listed below.
Pen drives barely allow any security system in terms of password or any other built in security feature. So it is more likely that if a person loses a pen drive, the data inside it can be accessed by anyone. If it falls in wrong hands he or she can misuse it. a pen drive can be easily stolen or misplaced and the data stored inside it can be easily manipulated. There have large demand for pen drives with some security systems such as finger-print reader or protective software.
There has been a conscious protest against pen drives in many private and government organization. Though it is a convenient device for the productive brains, it has proved to be beneficial for the thieves as well. Pen drives are small in size and have greater capacity to store information. Hence the thieves can carry the device stealthily in pockets and take information.
The threats that are associated with pen drives are serious. Some of them are listed below.
- Stealing of data
- Spreading virus
- Plant malicious software
- Causing data loss
Pen drives barely allow any security system in terms of password or any other built in security feature. So it is more likely that if a person loses a pen drive, the data inside it can be accessed by anyone. If it falls in wrong hands he or she can misuse it. a pen drive can be easily stolen or misplaced and the data stored inside it can be easily manipulated. There have large demand for pen drives with some security systems such as finger-print reader or protective software.
There has been a conscious protest against pen drives in many private and government organization. Though it is a convenient device for the productive brains, it has proved to be beneficial for the thieves as well. Pen drives are small in size and have greater capacity to store information. Hence the thieves can carry the device stealthily in pockets and take information.
Labels:
Technology,
Windows
Monday, November 24, 2008
Fetching a row from table(ispf) using rexx
This is a simple rexx code, to fetch a row from ispf table.
lets say the table name is "sample" & it has two columns "id" & "name"
id name
001 agent001
002 agent002
003 agent003
if u want to know the name of person with id = '001' . then this is a simple code.
/*REXX*/
TDSN = "aaa.dsn"
ID = '001'
ADDRESS ISPEXEC "CONTROL ERRORS RETURN"
ADDRESS ISPEXEC "LIBDEF ISPTLIB"
ADDRESS ISPEXEC "LIBDEF ISPTABL"
ADDRESS ISPEXEC "LIBDEF ISPTLIB DATASET ID ('"TDSN"') UNCOND"
ADDRESS ISPEXEC "LIBDEF ISPTABL DATASET ID ('"TDSN"') UNCOND"TNAME = "SAMPLE"
ADDRESS ISPEXEC "TBCLOSE "TNAME
ADDRESS ISPEXEC "TBOPEN "TNAME
ADDRESS ISPEXEC "TBTOP "TNAME
ADDRESS ISPEXEC "TBSCAN "TNAME" ARGLIST ( ID )"
ADDRESS ISPEXEC "TBGET " TNAME
VARNAME = NAME
ADDRESS ISPEXEC "TBCLOSE "TNAME
ADDRESS ISPEXEC "LIBDEF ISPTLIB"
ADDRESS ISPEXEC "LIBDEF ISPTABL" SAY VARNAME
result : agent001
lets say the table name is "sample" & it has two columns "id" & "name"
id name
001 agent001
002 agent002
003 agent003
if u want to know the name of person with id = '001' . then this is a simple code.
/*REXX*/
TDSN = "aaa.dsn"
ID = '001'
ADDRESS ISPEXEC "CONTROL ERRORS RETURN"
ADDRESS ISPEXEC "LIBDEF ISPTLIB"
ADDRESS ISPEXEC "LIBDEF ISPTABL"
ADDRESS ISPEXEC "LIBDEF ISPTLIB DATASET ID ('"TDSN"') UNCOND"
ADDRESS ISPEXEC "LIBDEF ISPTABL DATASET ID ('"TDSN"') UNCOND"TNAME = "SAMPLE"
ADDRESS ISPEXEC "TBCLOSE "TNAME
ADDRESS ISPEXEC "TBOPEN "TNAME
ADDRESS ISPEXEC "TBTOP "TNAME
ADDRESS ISPEXEC "TBSCAN "TNAME" ARGLIST ( ID )"
ADDRESS ISPEXEC "TBGET " TNAME
VARNAME = NAME
ADDRESS ISPEXEC "TBCLOSE "TNAME
ADDRESS ISPEXEC "LIBDEF ISPTLIB"
ADDRESS ISPEXEC "LIBDEF ISPTABL" SAY VARNAME
result : agent001
Labels:
REXX
Saturday, November 22, 2008
JBoss is loosing its charm ?
Jboss is certainly facing an evolution competitive front, and basically has not reponded to it.
The competitive fronts are two-fold, and will be recognizable by even the most passing of observers in the middleware market.
1. Seam is losing month-by-month to Spring
2. Jboss is losing month-by-month to Glassfish
Here are some of the proof-points, first the JCP page for Web Beans, the standardization process of Seam:
http://jcp.org/en/jsr/detail?id=299
It shows a slower growth, while Spring rolls out S2AP and myriad other complementary technologies to seize the develper's attention. Seam is dying on the vine, and its own complexity does not bode well for a major roll-out of improvements any time soon
Just look at jboss.org, it is a mind -numbing array of ongoing and outstanding projects with SSO, ESB, and Rules among others seemingly having no delivery date in sight, that translates to project stability. This makes us to think whether JBoss products and projects is under-resourced?
The competitive fronts are two-fold, and will be recognizable by even the most passing of observers in the middleware market.
1. Seam is losing month-by-month to Spring
2. Jboss is losing month-by-month to Glassfish
Here are some of the proof-points, first the JCP page for Web Beans, the standardization process of Seam:
http://jcp.org/en/jsr/detail?id=299
It shows a slower growth, while Spring rolls out S2AP and myriad other complementary technologies to seize the develper's attention. Seam is dying on the vine, and its own complexity does not bode well for a major roll-out of improvements any time soon
Just look at jboss.org, it is a mind -numbing array of ongoing and outstanding projects with SSO, ESB, and Rules among others seemingly having no delivery date in sight, that translates to project stability. This makes us to think whether JBoss products and projects is under-resourced?
Labels:
Server,
Technology
Thursday, November 20, 2008
AMD seeks redemption with ‘Shanghai’ chip
Let bygones be bygones. That's what Advanced Micro Devices is hoping for with the roll-out of its first 45-nanometer processor Thursday. The No. 2 PC processor supplier will make the case that Shanghai is not Barcelona. The latter chip–AMD's first quad-core processor–was rolled out in September 2007 to great fanfare but then faced prolonged delays. This gave Intel an opportunity to regain ground it had lost to AMD in the server chip market. Shanghai is not a new architecture but essentially a refresh of AMD's Barcelona Opteron chip. AMD claims Shanghai is 35 percent faster than Barcelona. The chip is being built on 45-nanometer process technology, while Barcelona was a 65-nanometer part. Typically, the smaller the geometries, the faster and more power efficient the processor
More >> http://news.cnet.com/8301-13924_3-10095649-64.html?tag=newsEditorsPicksArea.0
More >> http://news.cnet.com/8301-13924_3-10095649-64.html?tag=newsEditorsPicksArea.0
Labels:
Technology
Wednesday, November 19, 2008
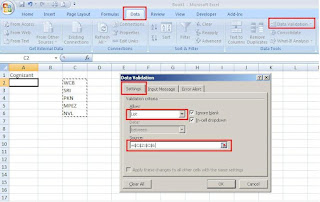
Excel - Tip -2
Excel enables us to restrict the values a user can enter in a cell. by restricting the values, we can ensure that our workbook entries are valid and also the calculations based on them are valid.
Follow these simple steps:
To create a validation list, we first need to type the values we want to include in the adjacent cells in a column or a row.
1. Click on the cell, in which we want to create a validation list.
2. Click on "Data" tab
3. Click on "Data Validation" option.
4. In the "Data Validation" dialog box, select "Settings" tab
5. Select the "List" option from the "Allow" drop down list.
6. Click in the "Source" field and Click & drag the validation entries (the one we have entered in the excel file)
7. Click on "Ok" button.
Now, the Excel will create the validation list, in the cell we have selected it.
Follow these simple steps:
To create a validation list, we first need to type the values we want to include in the adjacent cells in a column or a row.
1. Click on the cell, in which we want to create a validation list.
2. Click on "Data" tab
3. Click on "Data Validation" option.
4. In the "Data Validation" dialog box, select "Settings" tab
5. Select the "List" option from the "Allow" drop down list.
6. Click in the "Source" field and Click & drag the validation entries (the one we have entered in the excel file)
7. Click on "Ok" button.
Now, the Excel will create the validation list, in the cell we have selected it.
Saturday, November 15, 2008
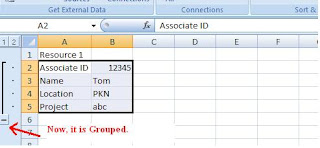
Excel tip -1
Hide Rows by Grouping
Using the Grouping option present in the Excel, we can hide the set of rows / columns.
Follow these steps,
1. Select the rows / columns that we need to hide.
2. Click on "Data" tab
3. Click on "Group" option
4. In the Group dialog box, select Rows/Columns option.
5. Click on OK button
Now, the Excel will create a clickable button on the far left or top of the worksheet. The button displayed either minus or a plus sign, depending on what is displayed in the worksheet
Using the Grouping option present in the Excel, we can hide the set of rows / columns.
Follow these steps,
1. Select the rows / columns that we need to hide.
2. Click on "Data" tab
3. Click on "Group" option
4. In the Group dialog box, select Rows/Columns option.
5. Click on OK button
Now, the Excel will create a clickable button on the far left or top of the worksheet. The button displayed either minus or a plus sign, depending on what is displayed in the worksheet

Wednesday, November 12, 2008
A wonderful tool in Excel!
Having used Microsoft Excel for presenting reports in the client's side, I wanted to share how wonderful a tool this is. Arguably, it is a tool used at some level by most people in an IT organization. Be it creating simple reports, business presentations using its versatile charts or even creating some simple birthday party accounts, Excel is a very important tool in MS Office suite of applications.
While Excel's worksheet formulas are being used extensively, its VBA properties, if harnessed properly, are much more rewarding. Hence, a little bit about learning VBA for somebody who will be interested -
For a set of tasks to be performed, select Tools –> Macros –> Record Macro (Office 2003) or Developer –> Record Macro (Office 2007) and then start doing what you want to do. Stop the recording and then open the Macro editor (Alt + F11). You will find the code recorded for the steps you had went through. This will be a very good starting place to explore and leverage this wonderful tool. Using the VBA help next will help fine tune the skill…
While Excel's worksheet formulas are being used extensively, its VBA properties, if harnessed properly, are much more rewarding. Hence, a little bit about learning VBA for somebody who will be interested -
For a set of tasks to be performed, select Tools –> Macros –> Record Macro (Office 2003) or Developer –> Record Macro (Office 2007) and then start doing what you want to do. Stop the recording and then open the Macro editor (Alt + F11). You will find the code recorded for the steps you had went through. This will be a very good starting place to explore and leverage this wonderful tool. Using the VBA help next will help fine tune the skill…
Labels:
Desktop,
MS Office,
Software,
Technology,
Windows
Sunday, November 09, 2008
Make a Step to SWITCH OFF…
Nowadays, we face lot of power cuts. We are worried about power cuts. All the weekdays we keep our self cool in Office. As soon as we reach home, our hands are in search of our Fan/Ac Switch…
The Next minute the power is off, we get irritated. We curse the EB Dept, Govt. and many others…. Do we ever care for switching off electrical items, after the use.
Have you ever noticed the street Lamps Glowing after 6.00 Am?
If yes, have you made an attempt to switch it off? Or
At least to make a complaint on this, to the Municipality?
Our duty not only ends in casting a vote to a person.
Whenever there is a problem. At the Max we do is getting frustrated, curse the people and walk off.
It’s every individual’s duty to take the responsibility for things happening around him/her.I don’t say that we should jump in streets and fight for the power cuts?
At Least make a step to put the Switches off…
The Next minute the power is off, we get irritated. We curse the EB Dept, Govt. and many others…. Do we ever care for switching off electrical items, after the use.
Have you ever noticed the street Lamps Glowing after 6.00 Am?
If yes, have you made an attempt to switch it off? Or
At least to make a complaint on this, to the Municipality?
Our duty not only ends in casting a vote to a person.
Whenever there is a problem. At the Max we do is getting frustrated, curse the people and walk off.
It’s every individual’s duty to take the responsibility for things happening around him/her.I don’t say that we should jump in streets and fight for the power cuts?
At Least make a step to put the Switches off…
Saturday, November 08, 2008
Insertion Sort Implementation
Insertion sort is a simple sorting algorithm, a comparison sort in which the sorted array (or list) is built one entry at a time. It is much less efficient on large lists than the more advanced algorithms such as quicksort, heapsort, or merge sort, but it has various advantages:
- Simple to implement
- Efficient on (quite) small data sets
- Efficient on data sets which are already substantially sorted
- More efficient in practice than most other simple O(n2) algorithms such as selection sort or bubble sort: the average time is n2/4 and it is linear in the best case
- Stable (does not change the relative order of elements with equal keys)
- In-place (only requires a constant amount O(1) of extra memory space)
- It is an online algorithm, in that it can sort a list as it receives it.
In abstract terms, each iteration of an insertion sort removes an element from the input data, inserting it at the correct position in the already sorted list, until no elements are left in the input. The choice of which element to remove from the input is arbitrary and can be made using almost any choice algorithm.
The following method shows how to implement insertion sort with Java:
public static void insertionSort( Comparable [ ] a )
{
for( int p = 1; p <>
{
Comparable tmp = a[ p ];
int j = p;
for( ; j > 0 && tmp.compareTo( a[ j - 1 ] ) <>
a[ j ] = a[ j - 1 ];
a[ j ] = tmp;
}
}
Source: java-tips.org
Labels:
Java,
Programming
Friday, November 07, 2008
CHANGING DOS BACKGROUND
To Change a DOS background.
- Open your registry --> press win+r and type regedit --> hit enter.
- goto
[HKEY_CURRENT_USER\Software\Microsoft\Command Processor] - You'll find "DefaultColor"
- You can replace it's value with a two-digit hexadecimal number, in which the first digit selects a background color and the second a foreground color.
The hexadecimal codes are:
Hexadecimal_value Color
- 0 Black
- 1 Blue
- 2 Green
- 3 Aqua
- 4 Red
- 5 Purple
- 6 Yellow
- 7 White
- 8 Gray
- 9 Light Blue
- A Light Green
- B Light Aqua
- C Light Red
- D Light Purple
- E Light Yellow
- F Bright White
Sample: A value of F0, for example, would give black text on a white background
Tuesday, November 04, 2008
Run Commands in Windows
Run Commands in Windows :
Do you use the Run feature in Windows XP? For most, this feature remains unused (or rarely used). Why is that? Well, first off nearly all of the Run Commands Correspond to a particular Control Panel Item or a Utility, Tool or Task that can be accessed through Windows.
Here is the list of different Run command. To access go to run (Win + R )
Accessibility Controls : access.cpl
Accessibility Wizard : accwiz
Add Hardware Wizard : hdwwiz.cpl
Add/Remove Programs : appwiz.cpl
Administrative Tools control : admintools
Adobe Acrobat (if installed) : acrobat
Adobe Designer (if installed) : acrodist
Adobe Distiller (if installed) : acrodist
Adobe ImageReady (if installed) : imageready
Adobe Photoshop (if installed) : photoshop
Automatic Updates : wuaucpl.cpl
Bluetooth Transfer Wizard : fsquirt
Calculator : calc
Certificate Manager : certmgr.msc
Character Map : charmap
Check Disk Utility : chkdsk
Clipboard Viewer : clipbrd
Command Prompt : cmd
Component Services : dcomcnfg
Computer Management : compmgmt.msc
Control Panel : control
Date and Time Properties : timedate.cpl
DDE Shares : ddeshare
Device Manager : devmgmt.msc
Direct X Control Panel (If Installed)* : directx.cpl
Direct X Troubleshooter : dxdiag
Disk Cleanup Utility : cleanmgr
Disk Defragment : dfrg.msc
Disk Management : diskmgmt.msc
Disk Partition Manager : diskpart
Display Properties control : desktop
Display Properties : desk.cpl
Display Properties (w/Appearance Tab Preselected) control : color
Dr. Watson System Troubleshooting Utility : drwtsn32
Driver Verifier Utility : verifier
Event Viewer : eventvwr.msc
Files and Settings Transfer Tool : migwiz
File Signature Verification Tool : sigverif
Findfast : findfast.cpl
Firefox (if installed) : firefox
Folders Properties control : folders
Fonts control : fonts
Fonts Folder : fonts
Free Cell Card Game : freecell
Game Controllers : joy.cpl
Group Policy Editor (XP Prof) : gpedit.msc
Hearts Card Game : mshearts
Help and Support : helpctr
HyperTerminal : hypertrm
Iexpress Wizard : iexpress
Indexing Service : ciadv.msc
Internet Connection Wizard : icwconn1
Internet Explorer : iexplore
Internet Properties : inetcpl.cpl
Internet Setup Wizard : inetwiz
IP Configuration (Display Connection Configuration) : ipconfig /all
IP Configuration (Display DNS Cache Contents) : ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents) : ipconfig /flushdns
IP Configuration (Release All Connections) : ipconfig /release
IP Configuration (Renew All Connections) : ipconfig /renew
IP Configuration (Refreshes DHCP & Re-Registers DNS) : ipconfig /registerdns
IP Configuration (Display DHCP Class ID) : ipconfig /showclassid
IP Configuration (Modifies DHCP Class ID) : ipconfig /setclassid
Java Control Panel (If Installed) : jpicpl32.cpl
Java Control Panel (If Installed) : javaws
Keyboard Properties control : keyboard
Local Security Settings : secpol.msc
Local Users and Groups : lusrmgr.msc
Logs You Out Of Windows : logoff
Malicious Software Removal Tool : mrt
Microsoft Access (if installed) : access.cpl
Microsoft Chat : winchat
Microsoft Excel (if installed) : excel
Microsoft Frontpage (if installed) : frontpg
Microsoft Movie Maker : moviemk
Microsoft Paint : mspaint
Microsoft Powerpoint (if installed) : powerpnt
Microsoft Word (if installed) : winword
Microsoft Syncronization Tool : mobsync
Minesweeper Game : winmine
Mouse Properties control : mouse
Mouse Properties : main.cpl
Nero (if installed) : nero
Netmeeting : conf
Network Connections control : netconnections
Network Connections : ncpa.cpl
Network Setup Wizard : netsetup.cpl
Notepad : notepad
Nview Desktop Manager (If Installed) : nvtuicpl.cpl
Object Packager : packager
ODBC Data Source Administrator : odbccp32.cpl
On Screen Keyboard : osk
Opens AC3 Filter (If Installed) : ac3filter.cpl
Outlook Express : msimn
Paint : pbrush
Password Properties : password.cpl
Performance Monitor : perfmon.msc
Performance Monitor : perfmon
Phone and Modem Options : telephon.cpl
Phone Dialer : dialer
Pinball Game : pinball
Power Configuration : powercfg.cpl
Printers and Faxes control : printers
Printers Folder : printers
Private Character Editor : eudcedit
Quicktime (If Installed) : QuickTime.cpl
Quicktime Player (if installed) : quicktimeplayer
Real Player (if installed) : realplay
Regional Settings : intl.cpl
Registry Editor : regedit
Registry Editor : regedit32
Remote Access Phonebook : rasphone
Remote Desktop : mstsc
Removable Storage : ntmsmgr.msc
Removable Storage Operator Requests : ntmsoprq.msc
Resultant Set of Policy (XP Prof) : rsop.msc
Scanners and Cameras : sticpl.cpl
Scheduled Tasks control : schedtasks
Security Center : wscui.cpl
Services : services.msc
Shared Folders : fsmgmt.msc
Shuts Down Windows : shutdown
Sounds and Audio : mmsys.cpl
Spider Solitare Card Game : spider
SQL Client Configuration : cliconfg
System Configuration Editor : sysedit
System Configuration Utility : msconfig
System File Checker Utility (Scan Immediately) : sfc /scannow
System File Checker Utility (Scan Once At Next Boot) : sfc /scanonce
System File Checker Utility (Scan On Every Boot) : sfc /scanboot
System File Checker Utility (Return to Default Setting) : sfc /revert
System File Checker Utility (Purge File Cache) : sfc /purgecache
System File Checker Utility (Set Cache Size to size x) : sfc /cachesize=x
System Information : msinfo32
System Properties : sysdm.cpl
Task Manager : taskmgr
TCP Tester : tcptest
Telnet Client : telnet
Tweak UI (if installed) : tweakui
User Account Management : nusrmgr.cpl
Utility Manager : utilman
Windows Address Book : wab
Windows Address Book Import Utility : wabmig
Windows Backup Utility (if installed) : ntbackup
Windows Explorer : explorer
Windows Firewall : firewall.cpl
Windows Magnifier : magnify
Windows Management Infrastructure : wmimgmt.msc
Windows Media Player : wmplayer
Windows Messenger : msmsgs
Windows Picture Import Wizard (need camera connected) : wiaacmgr
Windows System Security Tool : syskey
Windows Update Launches : wupdmgr
Windows Version (to show which version of windows) : winver
Windows XP Tour Wizard : tourstart Wordpad : write
Do you use the Run feature in Windows XP? For most, this feature remains unused (or rarely used). Why is that? Well, first off nearly all of the Run Commands Correspond to a particular Control Panel Item or a Utility, Tool or Task that can be accessed through Windows.
Here is the list of different Run command. To access go to run (Win + R )
Accessibility Controls : access.cpl
Accessibility Wizard : accwiz
Add Hardware Wizard : hdwwiz.cpl
Add/Remove Programs : appwiz.cpl
Administrative Tools control : admintools
Adobe Acrobat (if installed) : acrobat
Adobe Designer (if installed) : acrodist
Adobe Distiller (if installed) : acrodist
Adobe ImageReady (if installed) : imageready
Adobe Photoshop (if installed) : photoshop
Automatic Updates : wuaucpl.cpl
Bluetooth Transfer Wizard : fsquirt
Calculator : calc
Certificate Manager : certmgr.msc
Character Map : charmap
Check Disk Utility : chkdsk
Clipboard Viewer : clipbrd
Command Prompt : cmd
Component Services : dcomcnfg
Computer Management : compmgmt.msc
Control Panel : control
Date and Time Properties : timedate.cpl
DDE Shares : ddeshare
Device Manager : devmgmt.msc
Direct X Control Panel (If Installed)* : directx.cpl
Direct X Troubleshooter : dxdiag
Disk Cleanup Utility : cleanmgr
Disk Defragment : dfrg.msc
Disk Management : diskmgmt.msc
Disk Partition Manager : diskpart
Display Properties control : desktop
Display Properties : desk.cpl
Display Properties (w/Appearance Tab Preselected) control : color
Dr. Watson System Troubleshooting Utility : drwtsn32
Driver Verifier Utility : verifier
Event Viewer : eventvwr.msc
Files and Settings Transfer Tool : migwiz
File Signature Verification Tool : sigverif
Findfast : findfast.cpl
Firefox (if installed) : firefox
Folders Properties control : folders
Fonts control : fonts
Fonts Folder : fonts
Free Cell Card Game : freecell
Game Controllers : joy.cpl
Group Policy Editor (XP Prof) : gpedit.msc
Hearts Card Game : mshearts
Help and Support : helpctr
HyperTerminal : hypertrm
Iexpress Wizard : iexpress
Indexing Service : ciadv.msc
Internet Connection Wizard : icwconn1
Internet Explorer : iexplore
Internet Properties : inetcpl.cpl
Internet Setup Wizard : inetwiz
IP Configuration (Display Connection Configuration) : ipconfig /all
IP Configuration (Display DNS Cache Contents) : ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents) : ipconfig /flushdns
IP Configuration (Release All Connections) : ipconfig /release
IP Configuration (Renew All Connections) : ipconfig /renew
IP Configuration (Refreshes DHCP & Re-Registers DNS) : ipconfig /registerdns
IP Configuration (Display DHCP Class ID) : ipconfig /showclassid
IP Configuration (Modifies DHCP Class ID) : ipconfig /setclassid
Java Control Panel (If Installed) : jpicpl32.cpl
Java Control Panel (If Installed) : javaws
Keyboard Properties control : keyboard
Local Security Settings : secpol.msc
Local Users and Groups : lusrmgr.msc
Logs You Out Of Windows : logoff
Malicious Software Removal Tool : mrt
Microsoft Access (if installed) : access.cpl
Microsoft Chat : winchat
Microsoft Excel (if installed) : excel
Microsoft Frontpage (if installed) : frontpg
Microsoft Movie Maker : moviemk
Microsoft Paint : mspaint
Microsoft Powerpoint (if installed) : powerpnt
Microsoft Word (if installed) : winword
Microsoft Syncronization Tool : mobsync
Minesweeper Game : winmine
Mouse Properties control : mouse
Mouse Properties : main.cpl
Nero (if installed) : nero
Netmeeting : conf
Network Connections control : netconnections
Network Connections : ncpa.cpl
Network Setup Wizard : netsetup.cpl
Notepad : notepad
Nview Desktop Manager (If Installed) : nvtuicpl.cpl
Object Packager : packager
ODBC Data Source Administrator : odbccp32.cpl
On Screen Keyboard : osk
Opens AC3 Filter (If Installed) : ac3filter.cpl
Outlook Express : msimn
Paint : pbrush
Password Properties : password.cpl
Performance Monitor : perfmon.msc
Performance Monitor : perfmon
Phone and Modem Options : telephon.cpl
Phone Dialer : dialer
Pinball Game : pinball
Power Configuration : powercfg.cpl
Printers and Faxes control : printers
Printers Folder : printers
Private Character Editor : eudcedit
Quicktime (If Installed) : QuickTime.cpl
Quicktime Player (if installed) : quicktimeplayer
Real Player (if installed) : realplay
Regional Settings : intl.cpl
Registry Editor : regedit
Registry Editor : regedit32
Remote Access Phonebook : rasphone
Remote Desktop : mstsc
Removable Storage : ntmsmgr.msc
Removable Storage Operator Requests : ntmsoprq.msc
Resultant Set of Policy (XP Prof) : rsop.msc
Scanners and Cameras : sticpl.cpl
Scheduled Tasks control : schedtasks
Security Center : wscui.cpl
Services : services.msc
Shared Folders : fsmgmt.msc
Shuts Down Windows : shutdown
Sounds and Audio : mmsys.cpl
Spider Solitare Card Game : spider
SQL Client Configuration : cliconfg
System Configuration Editor : sysedit
System Configuration Utility : msconfig
System File Checker Utility (Scan Immediately) : sfc /scannow
System File Checker Utility (Scan Once At Next Boot) : sfc /scanonce
System File Checker Utility (Scan On Every Boot) : sfc /scanboot
System File Checker Utility (Return to Default Setting) : sfc /revert
System File Checker Utility (Purge File Cache) : sfc /purgecache
System File Checker Utility (Set Cache Size to size x) : sfc /cachesize=x
System Information : msinfo32
System Properties : sysdm.cpl
Task Manager : taskmgr
TCP Tester : tcptest
Telnet Client : telnet
Tweak UI (if installed) : tweakui
User Account Management : nusrmgr.cpl
Utility Manager : utilman
Windows Address Book : wab
Windows Address Book Import Utility : wabmig
Windows Backup Utility (if installed) : ntbackup
Windows Explorer : explorer
Windows Firewall : firewall.cpl
Windows Magnifier : magnify
Windows Management Infrastructure : wmimgmt.msc
Windows Media Player : wmplayer
Windows Messenger : msmsgs
Windows Picture Import Wizard (need camera connected) : wiaacmgr
Windows System Security Tool : syskey
Windows Update Launches : wupdmgr
Windows Version (to show which version of windows) : winver
Windows XP Tour Wizard : tourstart Wordpad : write
Labels:
Boot up,
Registry,
Software,
Technology,
Windows
Saturday, November 01, 2008
Unix Commands (Command line & Shell Script)
Here is an excellant article I found in IBM's Developerworks, which explains the basics of using commands in Command Line and while writing Shell Scripts.
http://www.ibm.com/developerworks/aix/library/au-spunix_clitricks/index.html?ca=drs-tp4008
Also I would recommend you to go through the articles in References section.
I'm not sure whether the Developerworks site has provided options to rise your doubts in the article's page iself so that the original author could respond to your queries. In case the option is not provided, do write your queries here I'll try to respond in this post.
http://www.ibm.com/developerworks/aix/library/au-spunix_clitricks/index.html?ca=drs-tp4008
Also I would recommend you to go through the articles in References section.
I'm not sure whether the Developerworks site has provided options to rise your doubts in the article's page iself so that the original author could respond to your queries. In case the option is not provided, do write your queries here I'll try to respond in this post.
Labels:
Desktop Unix,
Programming
Subscribe to:
Posts (Atom)


