Wednesday, April 15, 2009
How To free Your hard disk space?
If you are reading this for first time ,i am sure that 200-400 mb space in your computer is taken by temp files. so, go and delete these files by following methods:
1. Start Run Command. or press windows key + R at a time .it will open a dialog box ,type there %temp% and enter . It will open a folder. Delete all these files. It is of no use and taking your hard disk space.
2.Start Run Command. or press windows key + R at a time .it will open a dialog box ,type there prefetch and enter . It will open a folder. Delete all these files. It is of no use and taking your hard disk space.
Monday, April 13, 2009
Object Serialization
Java provides this facility through ObjectInput and ObjectOutput interfaces. The concrete implementation of ObjectOutput and OnjectInput interfaces is provided in ObjectOutputStream and ObjectInputStream classes respectively. These two interfaces have the following methods:
final void writeObject(Object obj) throws IOException
final Object readObejct() through IOException, ClassNotFoundException
The writeObject() method can be used be used to write any object to a stream, including strings and arrays and readObject() method can be used to read any stream as long as an object supports java.io.Serializable interface.
source: java-tips.org
Saturday, April 11, 2009
The private main method
I came across a good article while surfing on the net about main method being private. That means it works if written as: private static void main( String [] args )
Moreover, this method can also be activated by the VM, which actually breaks the encapsulation law. Actually, Sun introduced this problem in version 1.2 of Java and was not solved till 1.3. This is the case on MS Windows NT, Linux and Solaris. However, while running this code on Windows 2000 or XP gives the proper run time exception as "Main method not public".
check it on: http://developer.java.sun.com/developer/bugParade/bugs/4252539.html
This issue is a known problem with a bug report opened against it. However, Sun has closed the bug report and the problem will NOT be fixed, "The runtime allows call to private methods, because of reflection. Fixing it will cause potential troubles." This violates oop's basic concept, i.e. data encapsulation, you can declare the method as private to restrict its access from outside the class where it is declared, but in this case you can declare main method as private and still jvm can access the method. This is also a compatibility issue: with some JVM this work, but other JVMs might be confused.
However, this is not a big issue as only JVM can give the call to private main method and any other attemp to access it, will result in the compile time error.
I don't know whether the bug has been solved or not but it was giving runtime exception on my machine (XP) "Main method not public" and it might get execute on Solaris or Linux machine. But be careful while taking the certification exam. The proper answer to "How do you define a main method?" remains: "The method main must be declared public, static, and void."
Thursday, April 09, 2009
Send Email in Outlook without Using Mouse!!!
1.Use Alt+Tab to switch to Outlook.
2.If you’re looking at anything other than one of your mail folders (like your Calendar or Contacts), hit Ctrl+Shift+M to open a new mail message, otherwise just hit Ctrl+N.
3.You should now be looking at a blank email, with your cursor placed in the To: field. Type the recipients name (and if Outlook is connected to Microsoft Exchange Server and you’re emailing somebody in your organization, you can type their name and hit Ctrl+K, which will verify their address for you).
4.Use the TAB key to navigate between the CC:, BCC: and Subject fields, filling in as necessary. 5.Hit TAB to enter the main text area of the email, type the body of your message.
6.Invoke the SpellCheck utility using the F7 key. Use the TAB key to navigate, making changes as needed.
7.Once you’re ready to send, hit Ctrl+Enter.
8.Bask in the knowledge that you’ve just sent an email and your mouse is getting dusty!
Pretty simple, right? This process is a little weird at first (especially if you want to attach files, etc. - use Alt+I, F to do that), but once you’ve done it a few times, you’ll wonder how you ever got along without it!
Source:http://blog.crankingwidgets.com/2007/01/30/no-mouse-required-how-to-create-and-send-an-email-in-outlook-using-only-your-keyboard/
Tuesday, April 07, 2009
Magic Numbers
Source: Read in a Magazine called "Speed Mathematics"
Sunday, April 05, 2009
Writing a file in Java
import java.io.*;
public class FileOutput {
public static void main(String[] args) {
FileOutputStream fos;
DataOutputStream dos;
try {
File file= new File("C:\\MyFile.txt");
fos = new FileOutputStream(file);
dos=new DataOutputStream(fos);
dos.writeInt(2333);
dos.writeChars("Hello");
} catch (IOException e) {
e.printStackTrace();
}
}
}
source: java-tips.org
Friday, April 03, 2009
Recalling the Message From Sent Items !!!
1. Go to the Sent Items folder.
2. Find the message you want recalled and double-click it.
3. Go to the Actions menu and select Recall This Message.
4. To recall the message:
Select Delete unread copies of this message. (Note: the recipient needs to have Outlook opened for the message to be deleted)
To replace the message:
Select Delete unread copies and replace with a new message, click OK, and type your new message.
To be notified about the success of the recall or replacement:
Check the Tell me if recall succeeds or fails for each recipient check box.
5. Click OK.
UPDATE: How To Recall a Sent Message in Outlook 2007:
1. Click on Sent Items.
2. Find the message you want recalled and double-click it to open.
3. Go to the Actions menu -> other Actionh and select Recall This Message.
Thursday, April 02, 2009
Convert html file into js file
import java.io.*;
public class ChangeFileM {
public static void main(String[] args) {
try {
BufferedReader obj1 = new BufferedReader(new FileReader("c:\\terms and conditions.html"));
OutputStream os= new FileOutputStream(new File("c:\\out.js"));
PrintStream ps = new PrintStream(os);
String line;
String prefix="document.write('";
String sufix="');";
while ((line = obj1.readLine())!= null) {
line = prefix + line + sufix;
ps.println(line);
}
ps.close();
os.close();
obj1.close();
} catch (Exception e) {
}
}
}
source: java-tips.org
Tuesday, March 31, 2009
How to Backup Registry??
2.In the text box in the Run window, type regedit and click OK. This will open the Registry Editor program.
3.Navigate to the very top of the registry key branches until you reach Computer.
4.Highlight Computer by clicking on it once.
5.From the Registry Editor menu, choose File and then Export….
6.In the Export Registry File window that appears, choose a location to save the file in.
Note: I recommend choosing your desktop or the C:\ drive. Both are very easy to access if you run into problems later and need to use the file.
7.Locate the File name: text field and enter a name for the backup file.
Note: This name is for you to remember what the exported registry file is for. Since you're backing up the entire Windows XP Registry, I would recommend calling this file Registry Backup or something like that.
8.Click the Save button.
A Registration File with an REG file extension will be created in the location you chose in Step 6 and with the file name you chose in Step 7. Continuing the example from the last step, the file would be named Registry Backup.reg.
9.You can now make as many changes to any area of the registry that you want.
10.If after making your registry changes, you realize that they did not give you the results you were looking for, you can simply restore the entire Windows XP registry back to the point at which you backed it up.
Source: http://pcsupport.about.com/od/windowsxp/ht/backupxpreg.htm
Sunday, March 29, 2009
How to check whether the dataset is empty in rexx..
this is the main program calling the macro CHKSZ.
/*REXX*/
ADDRESS ISPEXEC "VIEW DATASET ('aaa.dataset')"
"MACRO(CHKSZ)"
ADDRESS ISPEXEC "VGET (SZ1) PROFILE"
IF SZ1 = 0
THEN SAY "EMPTY DATASET"
ELSE SAY "NONEMPTY DATASET" EXIT
MACRO(CHKSZ):
/*REXX*/
ADDRESS ISPEXEC "ISREDIT MACRO"
"ISREDIT (SZ1) = LINENUM .ZL"
ADDRESS ISPEXEC "VPUT (SZ1) PROFILE" "ISREDIT CANCEL"
Friday, March 27, 2009
New Twist in the Story
The man below says, 'Yes. You are in a hot air balloon, Hovering approximately 30 feet above this field. You are between 40 and 42 degrees North latitude, and between 58 and 60 degrees West Longitude.'
'You must be a programmer,' says the balloonist.
'I am,' replies the man. 'How did you know?'
'Well,' says the balloonist, 'everything you have told me is Technically correct, but I have no idea what to make of your Information and the fact is I am still lost.'
The man below says, "You must be a project manager."
'Yes, I am,' replies the balloonist, 'but how did you know?'
'Well,' says the man, 'you don't know where you are, or where You are going. You have made a promise which you have no idea how to Keep, and you expect me to solve your problem.'
Wednesday, March 25, 2009
Remove Flashing in Applet
1.Use Media Tracker for downloading the images.
2.Use double buffering.
3.Change the default background colour of the applet to the colour of you Canvas by using setBackground(Colour of the Canvas) in the init method of the applet.
4.In an animation if you are updating only part of a area use repaint(x1,y2,x2,y2) instead of repaint().
source: java-tips.org
Monday, March 23, 2009
Using execio to find a empty dataset
/*rexx*/
INPUT = "AAA.DSN"
INPUT = STRIP(INPUT)
IF SYSDSN("'"INPUT"'") = "OK" THEN
DO
"ALLOC FI(INDD) DA('"INPUT"') SHR REUSE" "EXECIO * DISKR INDD (FINIS STEM X."
IF X.0 = 0 THEN SAY "DATASET IS EMPTY"
IF X.0 \= 0 THEN SAY "DATASET IS NOT EMPTY"
END
ELSE SAY "INPUT DATASET DOESNOT EXIST"
Saturday, March 21, 2009
Automatic Deployment in OC4J
Automatic deployment, or OC4J Polling is a task management feature that automatically checks for changes made to currently deployed applications and modules, and reloads those files that have been modified. This functionality is a tremendous benefit for developers, eliminating the need to go through the deployment process every time code is updated.
Configuration and Limitations are explained in the link :
http://download.oracle.com/docs/cd/E12524_01/web.1013/e12289/autodeploy.htm
Thursday, March 19, 2009
JAVA IDE JDK SDK
JDK: JDK is the acronym for Java Design Kit which is a command line based interface to JVM.We are responsible for our own editors to creating a code for GUI elements.Most of the IDE ’s come with JDK and also their own JVM and Class Libraries.
SDK: SDK is the acronym for Software Development Kit , typically a set of development tools that allows us to create applications for a certain software package, software framework, hardware platform, computer system and video game console.
Tuesday, March 17, 2009
Use Keyboard For Right Click !!!
You can bring up the context menu on any selected item by pressing "Shift-F10".
This is exactly the same as right-clicking with the mouse, and should work almost anywhere that right-clicking works.
Sunday, March 15, 2009
Info about the Process running on your System
For information about the process, please refer the below URL:
http://www.processlibrary.com/
Friday, March 13, 2009
Run java through batch file
A simpler(& very simpler) 'fix' to this is to create a batch file with parameters:
1) Goto Start - run - "cmd"(enter)
2) c:\>Documents and Settings\(ur employee ID)> (Now if u want to store your .java files here then skip goto step 5)
3) c:\>Documents and Settings\(ur employee ID)> copy con s.bat (enter)
cd\
e:
cd
(press Ctrl+Z) to save the file.
4) c:\>Documents and Settings\(ur employee ID)> s (enter)
5) e:\>(foldername)> copy con j.bat (enter)
javac %1.java
java %1
(press Ctrl+Z) to save the file.
And there u go. Each time you want to runa .java file again….
just follow the below steps:
1)Goto cmd - s(enter)
e:\>(foldername)> j filename (enter)
The file runs. Very simple….and yet effective!!!
Wednesday, March 11, 2009
Create a Shortcut to Lock Your Computer!!
Right-click the desktop.Point to New, and then click Shortcut.
The Create Shortcut Wizard opens. In the text box, type the following:
- rundll32.exe user32.dll,LockWorkStation
- Click Next.
- Enter a name for the shortcut. You can call it "Lock Workstation" or choose any name you like.
- Click Finish.
- You can also change the shortcut's icon (my personal favorite is the padlock icon in shell32.dll).
- To change the icon:Right click the shortcut and then select Properties.
- Click the Shortcut tab, and then click the Change Icon button.In the Look for icons in this file text box, type:Shell32.dll.
- Click OK.
- Select one of the icons from the list and then click OK
You could also give it a shortcut keystroke such CTRL+ALT+L.
This would save you only one keystroke from the normal command, but it could be more convenient.
Note: If You still Find this as Difficult then Simply use the Key Stroke "Windows+L" to lock the computer.
Monday, March 09, 2009
Detect IP Address and Name in Java
import java.net.*;
public class IPAdress {
public static void main(String[] args) {
try {
System.out.println(InetAddress.getLocalHost().getHostName());
System.out.println(InetAddress.getLocalHost().getHostAddress());
}
catch (UnknownHostException e) {
e.printStackTrace();
}
}
}
source: java-tips.org
Friday, March 06, 2009
Clean-up the RAM
1.Open a notepad and type FREEMEM=SPACE(64000000).
2.Save the file as RAM.vbs and run the script.
Tuesday, March 03, 2009
Save your Nokia battery life
First of all you have to lock your keypad and then you can click the left soft key or the red button(anyone or both may work). Doing so will immediately switch off the backlight of your cell phone.
Although this may seem so simple, it saves about 10% of your battery every time and this decreases the no. of times that you will have to recharge your batteries thereby increasing your battery life…
This works in all smaller handsets upto 6233.
Sunday, March 01, 2009
Converting URI to URL
import java.net.*;
public class DemoConvertURItoURL {
public static void main(String[] args) {
URI uri = null;
URL url = null;
String uriString = "http://www.google.co.in/";
try {
uri = new URI(uriString);
}
catch (URISyntaxException e) {
e.printStackTrace();
}
try {
url = uri.toURL();
}
catch (IllegalArgumentException e) {
e.printStackTrace();
}
catch (MalformedURLException e) {
e.printStackTrace();
}
System.out.println("Original URI : " + uri);
System.out.println("Converted URL : " + url);
}
}
source: java-tips.org
Friday, February 27, 2009
Advantages of SQL server 2005 over SQL server 2000/ SQL server 7.0
- SQL server 2005 is exclusively designed for dot net developers. Whatever the function or procedure that we write in dot net environment those function or procedure that we directly execute in sql server environment. This is the new feature in SQL Server 2005.
- SQL Server 2005 has reduced application downtime, increased scalability and performance, and tight yet flexible security controls.
- SQL Server 2005 makes it simpler and easier to deploy, manage, and optimize enterprise data and analytical applications.
- It enables you to monitor, manage, and tune all of the databases in the effective way.
- Failure of the primary system, applications can immediately reconnect to the database on the secondary server using Database Mirroring.
- SQL Server 2005 provides a new capability for the partitioning of tables across file groups in a database.
- Has Features of XML, Multidimensional Expressions (MDX), and XML for Analysis (XMLA). Integration with the Visual Studio development environment provides more efficient development and debugging of line-of-business and business intelligence (BI) applications.
Wednesday, February 25, 2009
Making a file read only through Java
import java.io.File;
public class ReadOnlyExp {
public static void main(String[] args) {
File file=new File("c:\\MyFile");
file.setReadOnly();
}
}
source: java-tips.org
Sunday, February 22, 2009
Java on Mainframe OS
On one side, you have the highly robust and scalable mainframe. On the other, you have the flexibility of Java and the Web world. As noted above, a typical Web application would initiate a transaction that would do a one-off database access.
The Java solution to submit the batch jobs from a Z/OS mainframe.
package fileTransferProtocol;
import org.apache.commons.net.ftp.*;
import java.io.*;
public class FileTransferProtocol {
public static void main (String [ ] args) {
String serverName ="my.zos.mainframe" ;
String userName ="userid" ;
String password ="********" ;
FTPClient ftp = new FTPClient() ;
//Connect to the server
try {
ftp.connect (serverName) ;
String replyText =ftp.getReplyString() ;
System.out.println (replyText) ;
}
catch (Exception e) {
e.printStackTrace () ;
}
//Login to the server
try {
ftp.login (userName, password) ;
String replyText = ftp.getReplyString() ;
System.out.println (replyText);
} catch (Exception e) {
e.printStackTrace();
}
//Tell server that the file will have JCL records
try {
ftp.site ("filetype=jes") ;
String replyText = ftp.getReplyString() ;
System.out.println (replyText) ;
}
catch (Exception e) {
e.printStackTrace() ;
}
//Submit the job from the text file.Use \\ to avoid using escape notation
try {
FileInputStream inputStream = new FileInputStream ("C:\\job.txt") ;
ftp.storeFile (serverName,inputStream) ;
String replyText = ftp.getReplyString() ;
System.out.println (replyText) ;
}
catch (Exception e) {
e.printStackTrace() ;
}
//Quit the server
try {
ftp.quit();
}
catch (Exception e) {
e.printStackTrace() ;
}
}
}
Thursday, February 19, 2009
Queued sequential access method
QSAM files can be on tape, direct access storage devices (DASDs), unit-record devices, and terminals. QSAM processing is best for tables and intermediate storage.To process QSAM files in a program, a programmer could use COBOL language statements that:
1. Identify and describe the QSAM files in the ENVIRONMENT DIVISION and the DATA DIVISION.
2.Process the records in these files in the PROCEDURE DIVISION.
After a record is created, its length or its position in the file cannot be changed, and it cannot be deleted. QSAM files can, however, be updated on DASD (using REWRITE).The record definitions that are coded in COBOL program and the length of the variables read into and written from determines the amount of data transferred.
Ref:wikipedia
Monday, February 16, 2009
Listing all drives on a file system
File[] roots = File.listRoots();for(int i=0;i
System.out.println("Root["+i+"]:" + roots[i]);
source: java-tips.org
Friday, February 13, 2009
Comparison of Oracle, DB2 and SQL SERVER
In contrast, Oracle, DB2 runs in most of operating systems.
DB2 was originally designed to run on IBM mainframe systems and continues to be the premier database for those systems. It also dominates in hybrid environments where IBM mainframes and newer servers must coexist. Although it has a reputation for being expensive, it is also has a reputation for being reliable and easy to use.
Oracle has a huge installed base of customers and continues to dominate the marketplace, especially for Unix operating system. It is highly reliable, it is expensive and difficult to use.
SQL SERVER is widely used for small to medium sized departmental systems. It is inexpensive and easy to use, but it is also unreliable and for not scaling well for systems with a large number of users.
Wednesday, February 11, 2009
Advantage of ReadOnly over Constant variables in dotnet
EXAMPLE:
// Compile time constant:public const int _Millennium = 2000;
// Runtime constant:public static readonly int _ThisYear = 2004;
Also, you can use readonly values for instance constants, storing different values for each instance of a class type. Compile-time constants are, by definition, static constants.
Sunday, February 08, 2009
CONVERTING FAT32 to NTFS in Windows XP:
2. Else Press WIN+R key in the keyboard
3. In the command prompt window, type: convert drive_letter: /fs:ntfs
For example, typing convert D: /fs:ntfs would format drive D: with the ntfs format. You can convert FAT or FAT32 volumes to NTFS with this command.
Important Once you convert a drive or partition to NTFS, you cannot simply convert it back to FAT or FAT32. You will need to reformat the drive or partition which will erase all data, including programs and personal files, on the partition.
Thursday, February 05, 2009
Opening the same file for reading and writing
RandomAccessFile raf = new RandomAccessFile("filename.txt", "rw");
source : java-tips.org
Tuesday, February 03, 2009
Why toString() is used in Java
It has at least two different meanings:
Displaying: How the object should appear to the user, in the GUI, on a web page, etc. Inspection: How the object should appear in debug output, logs, debugger tools etc. Both are in some way “a string representation of the object”. The default implementation in java.lang.Object suggests inspection, e.g. “java.lang.Object@c37f31”, but many APIs, like AWT/Swing, use it for displaying the object to the user.
Problems: It’s hard to tell which usage is intended when reading the code. Debuggers will use toString(), which can cause confusing side-effects. Since every object has a toString(), the IDE’s usage search becomes unusable. It’s hard to tell if a toString() method is dead code or not. We can’t do much about java.lang.Object, but we still have options.
Suggestion: Use toString() only for logging and debug output.
If the method has a more specific meaning, communicate that instead, e.g. title() or name().
If the value to display has a specific format you can communicate that instead, e.g. toHTML() or asLeetSpeak().
If the value to display is nothing other than a string, still avoid toString(). Call it something like displayString(), or maybe even asString() to avoid problems.
Reference: http://java.sun.com/
Saturday, January 31, 2009
Factorial Implementation in java
This tip shows how to implement factorial function in Java.
public class Factorial
{
public static long factorial( int n )
{
if( n <= 1 )
return 1;
else
return n * factorial( n - 1 );
}
public static void main( String [ ] args )
{
for( int i = 1; i <= 10; i++ )
System.out.println( factorial( i ) );
}
}
Tuesday, January 27, 2009
Document Retrieval Concepts
Document: A unit of retrieval. It might be a paragraph, a section, a chapter, Web page, an article, a whole book, or images and video.
Index: A data structure built on the text to speed up searching.
Index Term( or keyword): A pre-selected term which can be used to refer to the content of a document. Usually, index terms are noun or noun groups. In the Web, however some search engines use all the words in a document as index terms.
Information Retrieval(IR): Part of computer science that studies the retrieval of information(not data) from a collection of written documents. The retrieved documents aim at satisfying a user information need usually expressed in natural language.
Logical view of documents: The representation of documents and Web pages adopted by the system. The most common form is to represent the text of the document by a set of terms or keywords.
Precision: An information retrieval performance measure that quantifies the fraction of retrieved documents which are known to be relevant.
Query: The expression of the user information need in the input language provided by the information system. The most common type of input language simply allows the specification of keywords and of a few Boolean connectives.
Recall: An information retrieval performance measure that quantifies the fraction of known relevant documents which were effectively retrieved.
Monday, January 26, 2009
Watch YouTube Videos in Gmail Chats
When someone sends you a YouTube link, you’ll now get a thumbnail preview of the video. Click play and another box will open up inside of Gmail that streams it. For additional options like full screen mode, embedding, or adding the video to your favorites, you’ll still need to click over to YouTube.
Saturday, January 24, 2009
Closing your connections
In any JMS operation, you would
a) open a connection to the JMS resource,
b) establish a session and
c) create a producer or a consumer to send or receive messages.
When you create a JMS connection, the container allocates resources on the resource provider. Therefore, the application should be responsible for ensuring that these resources are de-allocated at the end of the operation. From a programming context, this is achieved by calling connection.close().
The application should ensure that the connection.close() is being called irrespective of the outcome of the operation. i.e., it should be called even under exception scenarios. This is typically achieved by closing the connection inside the finally block.
There is generally a confusion about whether closing a connection alone is sufficient or whether the underlying session and the message producer or message consumer should also be closed. The JMS 1.1 spec clearly states that closing a connection alone is sufficient. When a connection.close() is invoked it tells the container that all the constituent objects of that connection should also be closed.
Now, once we have coded everything correctly, we should make sure that we are not leaking connections. How do we identify that? There are a couple of unix commands that I use to make sure that my code is not leaking connections. When we open a connection, a TCP communication channel is opened between your application and the resource provider. In the case of AQ, it is a connection from your JVM to the AQ database. So if we monitor the number of connections that are open between your server and the AQ database, we can find out if there is a leak or not.
One way is to use the netstat command. You can use netstat -an grep 1521 grep dbhost wc -l to get the number of connections opened from your server to the AQ database.
But there is a problem here. We have multiple oc4js running from 1 server. So we will not be able to identify whether the connections are coming from your oc4j or another oc4j. There is another command in unix called lsof which lists all the open files. In unix, a socket is again a file. If you execute the command lsof -i :1521 grep dbhost grep pid wc -l it will give the number of open connections from your oc4j to the AQ database. Here pid is the process id of your oc4j.
Give it a try and let me know your thoughts.
Wednesday, January 21, 2009
Simple e-Mail Etiquette
- Be concise and to the point
- Answer all questions, and pre-empt further questions
- Use proper spelling, grammar & punctuation
- Use templates for frequently used responses
- Do not attach unnecessary files
- Use proper structure & layout
- Do not overuse the high priority option
- Do not write in CAPITALS
- Don't leave out the message thread
- Read the email twice before you send it
- Use a meaningful subject
- Use Active Voice instead of Passive Voice
- Avoid long sentences.
Sunday, January 18, 2009
To use Notepad as a Log File!!!
2. Type .LOG (caps) as the first line of the file, followed by a enter. Save the file and close it.
3. Double-click the file to open it and notice that Notepad appends the current date and time to the end of the file and places the cursor on the line after.
4. Type your notes and then save and close the file.
5. Each time you open the file, Notepad repeats the process, appending the time and date to the end of the file and placing the cursor below it!
Source : Read in Chip Magazine of October 2008
Thursday, January 15, 2009
Ensure that table statistics are updated before performing a bind
This can be very expensive depending on the size of the table.
A quick and easy way to look at the statistics is to query the "sysibm.systables" catalog table for the specific table you are interested in and look for the values in columns CARD, NPAGES.
A value of -1 indicates that statistics have not been collected from the table/index and runstats needs to be run on the table.
If the values differ significantly from the number of rows in the table - once again a "runstats" may be necessary to update the catalog statistics.
Once the runstats process has been run, the bind should be performed again so that the optimizer takes advantage of the new statistics.
Monday, January 12, 2009
Change the size of icons in Start menu
1. Right click on Taskbar,
2. In new open window click on Start Menu,
3. Choose Customize,
4. In General Click in Large or Small icon,
5. Click on OK,
6. Again click on OK.
Source: Read in a Magazine
Friday, January 09, 2009
Sending broadcast packets in Java
So, sending a broadcast packet from a Java program (or from a program in any other language, for that matter) simply requires you to specify the broadcast address as the destination for the packet.
Source: java-tips.org
Tuesday, January 06, 2009
Disabling My Computer
To disable this:
1.Open RegEdit
2.Search for 20D04FE0-3AEA-1069-A2D8-08002B30309D
3.This should bring you to the HKEY_CLASSES_ROOT\CLSID section
4.Delete the entire section.
Now when you click on My Computer, nothing will happen.
You might want to export this section to a Registry file before deleting it just in case you want to enable it again. Or you can rename it to 20D0HideMyComputer4FE0-3AEA-1069-A2D8-08002B30309D. You can also hide all the Desktop Icons, see Change/Add restrictions.
Saturday, January 03, 2009
How to Change User Password at Command Prompt
"net user * /domain" (without the quotation marks)
When you are prompted to type a password for the user, type the new password, not the existing password. After you type the new password, the system prompts you to retype the password to confirm. The password is now changed.
Alternatively, you can type the following command: net user . When you do so, the password changes without prompting you again. This command also enables you to change passwords in a batch file.
Non-administrators receive a "System error 5 has occurred. Access is denied" error message when they attempt to change the password.
Wednesday, December 31, 2008
Debugging ColdFusion
1.By specifying the DEBUG attribute in
2.By enabling server side debugging in ColdFusion Administrator panel.
For instance,
SELECT Distributor.Distributor_ID,
Distributor.Distributor_Name FROM Distributor ORDER BY Distributor.Distributor_ID
Tuesday, December 30, 2008
Hide Quick Navigation Bar
Copy the above code lines and add a content editor webpart to any of the webpart Zone and past the copied above lines, you also make visible false of the webpart.
Monday, December 29, 2008
C# Brainteasers
What does it do?
using System;
using System.Collections.Generic;
class Test{
delegate void Printer();
static void Main() {
List
for (int i=0; i <>
{
printers.Add(delegate { Console.WriteLine(i); } );
}
foreach (Printer printer in printers)
{
printer();
}
}
}
Saturday, December 27, 2008
Cellphone Hazards
Four times the radiation is leaked into the side of the head than is actually being used to transmit a signal. Highest emission comes from the antenna region. The reason for the leakage is that manufacturers tend to lower down the production cost, in exchange of lessening down the radiation that would escape into the user’s head and lowering down possible risks, thus the source of leakage: poorly matched transmitters, feeds and antennas. It must also be blamed to the lack of shielding in the phone case.
It is important that mobile phone manufacturers should be alarmed with this scenario and start designing cell phones that will not endanger the health of users. Make sure that all cellphones are sold with head sets or earphones. In this way, the user will have the option of not using the cellphone close to his head. The truth is, the essential key to safety lies to the manufacturers themselves, by designing safety features that will help protect and reassure their customers.
This information is from Sciencetips.com
Tuesday, December 23, 2008
Resolving the newfolder.exe virus
This virus is know popularly as regsvr.exe virus, or as new folder.exe virus and most people identify this one by seeing autorun.inf file on their pen drives. It is spreading mostly using pen drives as the medium.
So I will tell you that how to remove this virus manually.
I prefer manual process simply because it gives me option to learn new things in the process.
- Search for autorun.inf file. It is a read only file so you will have to change it to normal by right clicking the file , selecting the properties and un-check the read only option.
- Open the file in notepad and delete everything and save the file.
- Now change the file status back to read only mode so that the virus could not get access again.
- Click start->run and type msconfig and click ok
- Go to startup tab look for regsvr and uncheck the option click OK.
- Click on Exit without Restart.
- Now go to control panel -> scheduled tasks, and delete the At1 task.
- Click on start -> run and type gpedit.msc and click Ok.
- Go to users configuration->Administrative templates->system Find “prevent access to registry editing tools” and change the option to disable.
- Once you do this you have registry access back.
- Click on start->run and type regedit and click ok
- Go to edit->find and start the search for regsvr.exe,
- Delete all the occurrence of regsvr.exe; remember to take a backup before deleting.
- Don't delete the regsvr32.exe.
- Delete regsvr.exe occurrences only.
- At one or two places you will find it after explorer.exe in theses cases only delete the regsvr.exe part and not the whole part. E.g. Shell = “Explorer.exe regsvr.exe” the just delete the regsvr.exe and leave the explorer.exe
- Click on start->search->for files and folders. Their click all files and folders Type “*.exe” as filename to search for
- Click on ‘when was it modified ‘ option and select the specify date option Type from date as 10/16/2008 and also type To date as 10/16/2008
- Now hit search and wait for all the exe’s to show up.
- Once search is over select all the exe files and shift+delete the files, caution must be taken so that you don’t delete the legitimate exe file.
- Also find and delete regsvr.exe, svchost .exe
Source for this post:
http://amiworks.co.in/talk/how-to-remove-new-folderexe-or-regsvrexr-or-autoruninf-virus/
Saturday, December 20, 2008
Search a User By name & get his ID on Unix
echo "Enter User Name to be Searched"
read USERNAME
NAMES=`who awk {'print $1'} sort -u`
for NAME in $NAMES
do
USER=`finger $NAMEgrep $USERNAME awk {'print $7,$8'}`
if [ "$USER" != "" ]
then
echo $USER ——- $NAME
fi
done
Wednesday, December 17, 2008
Searching lines before & After in Unix
#———————————————–
#Program used to search a seed in a program
#———————————————–
SEED=$1
LINE=$2
FILE1=$3
for X in `awk '/'"$SEED"'/{ print NR }' $FILE1 `
do
echo ———————– $SEED ————————————–
NOB=`expr $X - $LINE`
NOA=`expr $X + $LINE`
if [ $NOB -lt 1 ]; then NOB=1
fi
for J in `awk 'NR == '"$NOB"',NR == '"$NOA"'
{
if(NF!=0) print; else print "\n"
}' $FILE1 `
do
echo $J
done
echo ——————————————————————-
done
Monday, December 15, 2008
Deploying J2EE applications on JBOSS Application Server
Step2 : Bring down the JBOSS Application server, Copy J2EE files like WAR/JAR/EAR/SAR/ZIP/RAR/JSE or xxx-ds.xml (data source) under the deploy directory
Step3:
Bring up the JBOSS Application service after deployment, follow the steps in 6.1.2
Go to
Open console.log and check whether J2EE files are deployed successfully
Note: Application stop/start is not required if it is a Hot deployment.
Saturday, December 13, 2008
ROUND() function in sql
ROUND ( numeric_expression , length [ ,function ] )
numeric_expression Is an expression of the exact numeric or approximate numeric data type category, except for the bit data type.
length Is the precision to which numeric_expression is to be rounded. length must be an expression of type tinyint, smallint, or int. When length is a positive number, numeric_expression is rounded to the number of decimal positions specified by length. When length is a negative number, numeric_expression is rounded on the left side of the decimal point, as specified by length.
function Is the type of operation to perform. function must be tinyint, smallint, or int. When function is omitted or has a value of 0 (default), numeric_expression is rounded. When a value other than 0 is specified, numeric_expression is truncated.
SELECT ROUND(column_name,decimals) FROM table_name
Parameter Description column_name Required. The field to round. decimals Required. Specifies the number of decimals to be returned.
1. SELECT ROUND(10.09 ,1) = 10.1
2. SELECT ROUND(10.09 ,-1) = 10
Thursday, December 11, 2008
Want to make money with the iPhone SDK ?
Here is one tutorial on writing an iPhone app:
http://www.cimgf.com/2008/10/01/cocoa-touch-tutorial-iphone-application-example/
So,if you want to start a ‘small scale IT business’ .This is one way now
Tuesday, December 09, 2008
SQL: Joins
Inner Join (simple join)Chances are, you've already written an SQL statement that uses an inner join. It is the most common type of join. Inner joins return all rows from multiple tables where the join condition is met.
Outer JoinAnother type of join is called an outer join. This type of join returns all rows from one table and only those rows from a secondary table where the joined fields are equal (join condition is met).
Sunday, December 07, 2008
Undraggable alert
Here is a code..you can try it
Script:
private function showAlert():void
{
title ="Undraggable Alert";
myAlert = Alert.show("HI Cognizant!!",title);
myAlert.isPopUp = false;
myAlert.status = Capabilities.version;
}
Friday, December 05, 2008
Difference Between URL and URI
URI - Uniform Resource Identifier
URL - Uniform Resource Locator
A URI _identifies_ a resource by meta-information of any kind.
A URL _locates_ a resource on the net, which means if you havea URL and the appropriate protocol you can retrieve the resource.
There are many different URI, e.g.:-
URL - Uniform Resource Locator
URC - Uniform Resource Characteristics
URN - Uniform Resource Names
One characteristic of a URI is, that it gives information aboutexactly one resource. Another is there can be more than one URIdescribing the same resource.
That was the theory, here is an example:
URI: <http://www.w3.org/>
URI: <http://www.w3.org/>
URL: http://www.w3.org/pub/WWW/>
All lines describing the same resource (the URL describes the location).
Wednesday, December 03, 2008
Levels in (service) Quality!
Level 1 - Criminal
Level 2 - Basic
Level 3 - Expected
Level 4 - Desired
Level 5 - Surprising
Level 6- Unbelievable!
(Think about it as how your client perceives the quality you deliver..the products you deliver..the services you deliver)
Monday, December 01, 2008
New iPod Touch faster than iPhone 3G
Apple appears to have upped the processing speed of the iPod Touch in order to help it go after the portable-game market.
Touch Arcade reports that the applications processor inside the second-generation iPod Touch unveiled in September is actually running faster than the processor inside the iPhone 3G, which runs at the same speed that the original iPhone and iPod Touch used. The new iPod Touch's ARM-based processor is running at 532MHz, while the iPhone 3G's processor runs at 412MHz.
A game developer interviewed by Touch Arcade noticed a huge difference in 3D-rendering speed as a result of the speed bump. As we remember fondly from our "megahertz madness" days of the Intel-AMD competition in the PC, processor speed is not the only measure of performance, but it is an important one.
With the arrival of the App Store, Apple has been marketing the latest iPod Touch as a gaming device in its latest round of commercials, almost completely ignoring the fact that it's a music and video player as well.
It seems that Apple has room to boost the clock speed of the processor to 620MHz, according to ARM's specifications, but that requires striking a balance between performance and battery life.
Saturday, November 29, 2008
select keyword in rexxx
syntax :
select
when cond1 then …
when cond2 then …
otherwise …
end
example :
/*rexx*/
number = 100
select
when number < 5 then say "less than 5" /*condition not sastisfied.this statement will not get executed*/
when number < 50 then say "less than 50" /*condition not sastisfied.this statement will not get executed*/
otherwise say "it should be greater than 50" /*condition sastisfied.this statement will get executed*/
end
Thursday, November 27, 2008
How to write a file in rexx
FILE = "N4C4F1.C3162.AUG13"
INPUT ="SAMPLE PROGRAM"
INPUT1 = "HOW TO WRITE a FILE"
INPUT2 = " THROUGH REXX"
DROP Z.
Z.1 = INPUT
Z.2 = INPUT1INPUT2
"ALLOC FI(OPDD) DA('"FILE"') SHR REUSE"
"EXECIO * DISKW OPDD (FINIS STEM Z."
Tuesday, November 25, 2008
Pen Drive -a part of Life
The threats that are associated with pen drives are serious. Some of them are listed below.
- Stealing of data
- Spreading virus
- Plant malicious software
- Causing data loss
Pen drives barely allow any security system in terms of password or any other built in security feature. So it is more likely that if a person loses a pen drive, the data inside it can be accessed by anyone. If it falls in wrong hands he or she can misuse it. a pen drive can be easily stolen or misplaced and the data stored inside it can be easily manipulated. There have large demand for pen drives with some security systems such as finger-print reader or protective software.
There has been a conscious protest against pen drives in many private and government organization. Though it is a convenient device for the productive brains, it has proved to be beneficial for the thieves as well. Pen drives are small in size and have greater capacity to store information. Hence the thieves can carry the device stealthily in pockets and take information.
Monday, November 24, 2008
Fetching a row from table(ispf) using rexx
lets say the table name is "sample" & it has two columns "id" & "name"
id name
001 agent001
002 agent002
003 agent003
if u want to know the name of person with id = '001' . then this is a simple code.
/*REXX*/
TDSN = "aaa.dsn"
ID = '001'
ADDRESS ISPEXEC "CONTROL ERRORS RETURN"
ADDRESS ISPEXEC "LIBDEF ISPTLIB"
ADDRESS ISPEXEC "LIBDEF ISPTABL"
ADDRESS ISPEXEC "LIBDEF ISPTLIB DATASET ID ('"TDSN"') UNCOND"
ADDRESS ISPEXEC "LIBDEF ISPTABL DATASET ID ('"TDSN"') UNCOND"TNAME = "SAMPLE"
ADDRESS ISPEXEC "TBCLOSE "TNAME
ADDRESS ISPEXEC "TBOPEN "TNAME
ADDRESS ISPEXEC "TBTOP "TNAME
ADDRESS ISPEXEC "TBSCAN "TNAME" ARGLIST ( ID )"
ADDRESS ISPEXEC "TBGET " TNAME
VARNAME = NAME
ADDRESS ISPEXEC "TBCLOSE "TNAME
ADDRESS ISPEXEC "LIBDEF ISPTLIB"
ADDRESS ISPEXEC "LIBDEF ISPTABL" SAY VARNAME
result : agent001
Saturday, November 22, 2008
JBoss is loosing its charm ?
The competitive fronts are two-fold, and will be recognizable by even the most passing of observers in the middleware market.
1. Seam is losing month-by-month to Spring
2. Jboss is losing month-by-month to Glassfish
Here are some of the proof-points, first the JCP page for Web Beans, the standardization process of Seam:
http://jcp.org/en/jsr/detail?id=299
It shows a slower growth, while Spring rolls out S2AP and myriad other complementary technologies to seize the develper's attention. Seam is dying on the vine, and its own complexity does not bode well for a major roll-out of improvements any time soon
Just look at jboss.org, it is a mind -numbing array of ongoing and outstanding projects with SSO, ESB, and Rules among others seemingly having no delivery date in sight, that translates to project stability. This makes us to think whether JBoss products and projects is under-resourced?
Thursday, November 20, 2008
AMD seeks redemption with ‘Shanghai’ chip
More >> http://news.cnet.com/8301-13924_3-10095649-64.html?tag=newsEditorsPicksArea.0
Wednesday, November 19, 2008
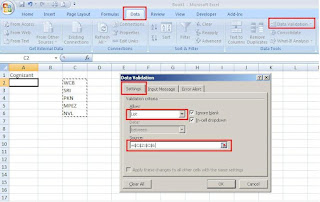
Excel - Tip -2
Follow these simple steps:
To create a validation list, we first need to type the values we want to include in the adjacent cells in a column or a row.
1. Click on the cell, in which we want to create a validation list.
2. Click on "Data" tab
3. Click on "Data Validation" option.
4. In the "Data Validation" dialog box, select "Settings" tab
5. Select the "List" option from the "Allow" drop down list.
6. Click in the "Source" field and Click & drag the validation entries (the one we have entered in the excel file)
7. Click on "Ok" button.
Now, the Excel will create the validation list, in the cell we have selected it.
Saturday, November 15, 2008
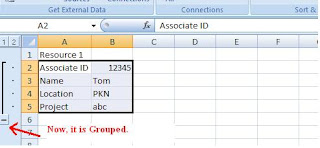
Excel tip -1
Using the Grouping option present in the Excel, we can hide the set of rows / columns.
Follow these steps,
1. Select the rows / columns that we need to hide.
2. Click on "Data" tab
3. Click on "Group" option
4. In the Group dialog box, select Rows/Columns option.
5. Click on OK button
Now, the Excel will create a clickable button on the far left or top of the worksheet. The button displayed either minus or a plus sign, depending on what is displayed in the worksheet

Wednesday, November 12, 2008
A wonderful tool in Excel!
While Excel's worksheet formulas are being used extensively, its VBA properties, if harnessed properly, are much more rewarding. Hence, a little bit about learning VBA for somebody who will be interested -
For a set of tasks to be performed, select Tools –> Macros –> Record Macro (Office 2003) or Developer –> Record Macro (Office 2007) and then start doing what you want to do. Stop the recording and then open the Macro editor (Alt + F11). You will find the code recorded for the steps you had went through. This will be a very good starting place to explore and leverage this wonderful tool. Using the VBA help next will help fine tune the skill…
Sunday, November 09, 2008
Make a Step to SWITCH OFF…
The Next minute the power is off, we get irritated. We curse the EB Dept, Govt. and many others…. Do we ever care for switching off electrical items, after the use.
Have you ever noticed the street Lamps Glowing after 6.00 Am?
If yes, have you made an attempt to switch it off? Or
At least to make a complaint on this, to the Municipality?
Our duty not only ends in casting a vote to a person.
Whenever there is a problem. At the Max we do is getting frustrated, curse the people and walk off.
It’s every individual’s duty to take the responsibility for things happening around him/her.I don’t say that we should jump in streets and fight for the power cuts?
At Least make a step to put the Switches off…
Saturday, November 08, 2008
Insertion Sort Implementation
- Simple to implement
- Efficient on (quite) small data sets
- Efficient on data sets which are already substantially sorted
- More efficient in practice than most other simple O(n2) algorithms such as selection sort or bubble sort: the average time is n2/4 and it is linear in the best case
- Stable (does not change the relative order of elements with equal keys)
- In-place (only requires a constant amount O(1) of extra memory space)
- It is an online algorithm, in that it can sort a list as it receives it.
In abstract terms, each iteration of an insertion sort removes an element from the input data, inserting it at the correct position in the already sorted list, until no elements are left in the input. The choice of which element to remove from the input is arbitrary and can be made using almost any choice algorithm.
The following method shows how to implement insertion sort with Java:
public static void insertionSort( Comparable [ ] a )
{
for( int p = 1; p <>
{
Comparable tmp = a[ p ];
int j = p;
for( ; j > 0 && tmp.compareTo( a[ j - 1 ] ) <>
a[ j ] = a[ j - 1 ];
a[ j ] = tmp;
}
}
Source: java-tips.org
Friday, November 07, 2008
CHANGING DOS BACKGROUND
- Open your registry --> press win+r and type regedit --> hit enter.
- goto
[HKEY_CURRENT_USER\Software\Microsoft\Command Processor] - You'll find "DefaultColor"
- You can replace it's value with a two-digit hexadecimal number, in which the first digit selects a background color and the second a foreground color.
The hexadecimal codes are:
Hexadecimal_value Color
- 0 Black
- 1 Blue
- 2 Green
- 3 Aqua
- 4 Red
- 5 Purple
- 6 Yellow
- 7 White
- 8 Gray
- 9 Light Blue
- A Light Green
- B Light Aqua
- C Light Red
- D Light Purple
- E Light Yellow
- F Bright White
Sample: A value of F0, for example, would give black text on a white background
Tuesday, November 04, 2008
Run Commands in Windows
Do you use the Run feature in Windows XP? For most, this feature remains unused (or rarely used). Why is that? Well, first off nearly all of the Run Commands Correspond to a particular Control Panel Item or a Utility, Tool or Task that can be accessed through Windows.
Here is the list of different Run command. To access go to run (Win + R )
Accessibility Controls : access.cpl
Accessibility Wizard : accwiz
Add Hardware Wizard : hdwwiz.cpl
Add/Remove Programs : appwiz.cpl
Administrative Tools control : admintools
Adobe Acrobat (if installed) : acrobat
Adobe Designer (if installed) : acrodist
Adobe Distiller (if installed) : acrodist
Adobe ImageReady (if installed) : imageready
Adobe Photoshop (if installed) : photoshop
Automatic Updates : wuaucpl.cpl
Bluetooth Transfer Wizard : fsquirt
Calculator : calc
Certificate Manager : certmgr.msc
Character Map : charmap
Check Disk Utility : chkdsk
Clipboard Viewer : clipbrd
Command Prompt : cmd
Component Services : dcomcnfg
Computer Management : compmgmt.msc
Control Panel : control
Date and Time Properties : timedate.cpl
DDE Shares : ddeshare
Device Manager : devmgmt.msc
Direct X Control Panel (If Installed)* : directx.cpl
Direct X Troubleshooter : dxdiag
Disk Cleanup Utility : cleanmgr
Disk Defragment : dfrg.msc
Disk Management : diskmgmt.msc
Disk Partition Manager : diskpart
Display Properties control : desktop
Display Properties : desk.cpl
Display Properties (w/Appearance Tab Preselected) control : color
Dr. Watson System Troubleshooting Utility : drwtsn32
Driver Verifier Utility : verifier
Event Viewer : eventvwr.msc
Files and Settings Transfer Tool : migwiz
File Signature Verification Tool : sigverif
Findfast : findfast.cpl
Firefox (if installed) : firefox
Folders Properties control : folders
Fonts control : fonts
Fonts Folder : fonts
Free Cell Card Game : freecell
Game Controllers : joy.cpl
Group Policy Editor (XP Prof) : gpedit.msc
Hearts Card Game : mshearts
Help and Support : helpctr
HyperTerminal : hypertrm
Iexpress Wizard : iexpress
Indexing Service : ciadv.msc
Internet Connection Wizard : icwconn1
Internet Explorer : iexplore
Internet Properties : inetcpl.cpl
Internet Setup Wizard : inetwiz
IP Configuration (Display Connection Configuration) : ipconfig /all
IP Configuration (Display DNS Cache Contents) : ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents) : ipconfig /flushdns
IP Configuration (Release All Connections) : ipconfig /release
IP Configuration (Renew All Connections) : ipconfig /renew
IP Configuration (Refreshes DHCP & Re-Registers DNS) : ipconfig /registerdns
IP Configuration (Display DHCP Class ID) : ipconfig /showclassid
IP Configuration (Modifies DHCP Class ID) : ipconfig /setclassid
Java Control Panel (If Installed) : jpicpl32.cpl
Java Control Panel (If Installed) : javaws
Keyboard Properties control : keyboard
Local Security Settings : secpol.msc
Local Users and Groups : lusrmgr.msc
Logs You Out Of Windows : logoff
Malicious Software Removal Tool : mrt
Microsoft Access (if installed) : access.cpl
Microsoft Chat : winchat
Microsoft Excel (if installed) : excel
Microsoft Frontpage (if installed) : frontpg
Microsoft Movie Maker : moviemk
Microsoft Paint : mspaint
Microsoft Powerpoint (if installed) : powerpnt
Microsoft Word (if installed) : winword
Microsoft Syncronization Tool : mobsync
Minesweeper Game : winmine
Mouse Properties control : mouse
Mouse Properties : main.cpl
Nero (if installed) : nero
Netmeeting : conf
Network Connections control : netconnections
Network Connections : ncpa.cpl
Network Setup Wizard : netsetup.cpl
Notepad : notepad
Nview Desktop Manager (If Installed) : nvtuicpl.cpl
Object Packager : packager
ODBC Data Source Administrator : odbccp32.cpl
On Screen Keyboard : osk
Opens AC3 Filter (If Installed) : ac3filter.cpl
Outlook Express : msimn
Paint : pbrush
Password Properties : password.cpl
Performance Monitor : perfmon.msc
Performance Monitor : perfmon
Phone and Modem Options : telephon.cpl
Phone Dialer : dialer
Pinball Game : pinball
Power Configuration : powercfg.cpl
Printers and Faxes control : printers
Printers Folder : printers
Private Character Editor : eudcedit
Quicktime (If Installed) : QuickTime.cpl
Quicktime Player (if installed) : quicktimeplayer
Real Player (if installed) : realplay
Regional Settings : intl.cpl
Registry Editor : regedit
Registry Editor : regedit32
Remote Access Phonebook : rasphone
Remote Desktop : mstsc
Removable Storage : ntmsmgr.msc
Removable Storage Operator Requests : ntmsoprq.msc
Resultant Set of Policy (XP Prof) : rsop.msc
Scanners and Cameras : sticpl.cpl
Scheduled Tasks control : schedtasks
Security Center : wscui.cpl
Services : services.msc
Shared Folders : fsmgmt.msc
Shuts Down Windows : shutdown
Sounds and Audio : mmsys.cpl
Spider Solitare Card Game : spider
SQL Client Configuration : cliconfg
System Configuration Editor : sysedit
System Configuration Utility : msconfig
System File Checker Utility (Scan Immediately) : sfc /scannow
System File Checker Utility (Scan Once At Next Boot) : sfc /scanonce
System File Checker Utility (Scan On Every Boot) : sfc /scanboot
System File Checker Utility (Return to Default Setting) : sfc /revert
System File Checker Utility (Purge File Cache) : sfc /purgecache
System File Checker Utility (Set Cache Size to size x) : sfc /cachesize=x
System Information : msinfo32
System Properties : sysdm.cpl
Task Manager : taskmgr
TCP Tester : tcptest
Telnet Client : telnet
Tweak UI (if installed) : tweakui
User Account Management : nusrmgr.cpl
Utility Manager : utilman
Windows Address Book : wab
Windows Address Book Import Utility : wabmig
Windows Backup Utility (if installed) : ntbackup
Windows Explorer : explorer
Windows Firewall : firewall.cpl
Windows Magnifier : magnify
Windows Management Infrastructure : wmimgmt.msc
Windows Media Player : wmplayer
Windows Messenger : msmsgs
Windows Picture Import Wizard (need camera connected) : wiaacmgr
Windows System Security Tool : syskey
Windows Update Launches : wupdmgr
Windows Version (to show which version of windows) : winver
Windows XP Tour Wizard : tourstart Wordpad : write
Saturday, November 01, 2008
Unix Commands (Command line & Shell Script)
http://www.ibm.com/developerworks/aix/library/au-spunix_clitricks/index.html?ca=drs-tp4008
Also I would recommend you to go through the articles in References section.
I'm not sure whether the Developerworks site has provided options to rise your doubts in the article's page iself so that the original author could respond to your queries. In case the option is not provided, do write your queries here I'll try to respond in this post.
Tuesday, October 28, 2008
How to Handle Apostophes in DB2
UPDATE EMPLOYEE SET EMPLY_NM = 's''atish' where EMPLY_ID =142082.
Just use the double quotes instead of single quote to avoid SQL error 'Unbalanced Apsotrphes'
The MF database will recognize the double quote as 'Apostophe'.
Where it will be useful:
when you are passing a input parametre value having apostophe to stored procedure or COBOL program,to update it into database.
Friday, October 24, 2008
Performance increase by Configuring Windows -MyComputer
Click on "Advanced" tab.
See the "performance" section? Click "Settings" > Disable all or some of the follwoing:
Fade or slide menus into view.
Fade or slide ToolTips into view.
Fade out menu items after clicking.
Show shadows under menus.
Slide open combo boxes.
Slide taskbar buttons.
Use a background image for each folder type.
Use common tasks in folders.
Tuesday, October 21, 2008
Environment Variables in Java
JAVA_HOME Should point to the folder above bin (eg.. C:\java )
If using ANT
ANT_HOME C:\java\apache-ant-1.7.0
If using Tomcat
CATALINA_HOME c:\tomcat6.0\tomcat
If using JIKES
JIKES_HOME c:\java\jikes-1.22
Sunday, October 19, 2008
Java on Ubuntu
The problem is, even after installing Sun's Java, GCJ is the default.
The default version of java can be changed using the update-java-alternatives command.
update-java-alternatives -l will give the list of all installed java packages.
example output:
java-1.5.0-sun 53 /usr/lib/jvm/java-1.5.0-sun
java-gcj 1042 /usr/lib/jvm/java-gcj
update-java-alternatives -s java-1.5.0-sun will set Sun's java as the default.
For some applications like Ant, Tomcat to run, you nee to set the JAVA_HOME environment variable like below
export JAVA_HOME=/usr/lib/jvm/java-1.5.0-sun
The above export can be put in /etc/bash.bashrc (for all users) or /home/
Friday, October 17, 2008
To remove shortcut icon arrows.
Go to {HKEY_CLASSES_ROOT\LNKFILE], and delete IsShortcut.
Go to [HKEY_CLASSES_ROOT\PIFFILE], and delete IsShortcut.
Wednesday, October 15, 2008
Keys for formatting data
ALT+' (apostrophe) - Display the Style dialog box
Friday, October 10, 2008
Memory Allocation of JVM
The follwoing code is to print Total,Free and Max memory allocated to JVM. it differs depends on the Java Environment.
Please have a look -
public class Memory {
/**
* @param args
*/
public static void main(String[] args) {
System.out.println("The Memory Allocation to JVM ");
long totalMemory = ((Runtime.getRuntime().totalMemory()/1024)/1024);
long freeMemory = ((Runtime.getRuntime().freeMemory()/1024)/1024);
long maxMemory = ((Runtime.getRuntime().maxMemory()/1024)/1024);
System.out.println("Total Memory::"+totalMemory+"MB");
System.out.println("Free Memory::"+freeMemory+"MB");
System.out.println("Max Memory::"+maxMemory+"MB");
}
}
Friday, October 03, 2008
DJ Java Decompiler
DJ Java Decompiler is a stand-alone Windows application; it doesn't require having Java installed! DJ Java Decompiler is not just Java decompiler and disassembler but it is also a fully featured Java editor using the graphic user interface with syntax-coloring. Using DJ Java Decompiler is easy. Select Open and load your desired class file, or just double-click the CLASS file you want to decompile. DJ Java Decompiler supports drag-and-drop functions for OLE. You will see the source code instantly! In Windows Explorer Right mouse-button pop-up menu available too.
You can decompile or disassembler a CLASS files on your computer hard disk or on a network drive that you have a connection to (you must have a full access rights or just change the default output directory for .jad files). You don't need to have the Java Virtual Machine or any other Java SDK installed. But this latest release is able to compile, run, create JAR archives and run applets outside of the context of a Web browser when JDK is installed. With DJ Java Decompiler you can decompile more than one java class file at one time.
Friday, September 19, 2008
Increase ur internet Speed by another tricks
Go to desktop->My computer-(right click on)->properties->then go HARDWARE tab->Device manager->Now u see a window of Device manager then go to Ports->Communication Port(double click on it and Open).
After open u can see a Communication Port properties.
Go the Port Setting:—-and now increase ur "Bits per second" to 128000 and "Flow control" change to Hardware.
Apply and see the result..
Monday, September 15, 2008
How to hide a file in image
1. Gather the file you wish to bind, and the image file, and place them in a folder. I will be using C:\New Folder-The image will hereby be referred to in all examples as fluffy.jpg-The file will hereby be referred to in all examples as New Text Document.txt
2. Add the file/files you will be injecting into the image into a WinRar .rar or .zip. From here on this will be referred to as (secret.rar)
3. Open command prompt by going to Start > Run > cmd
4. In Command Prompt, navigate to the folder where your two files are by typingcd location [ex: cd C:\New Folder]
5. Type [copy /b fluffy.jpg + secret.rar fluffy.jpg] (remove the brackets)
Congrats, as far as anyone viewing is concerned, this file looks like a JPEG, acts like a JPEG, and is a JPEG, yet it now contains your file.
In order to view/extract your file, there are two options that you can take
a) Change the file extension from fluffy.jpg to fluffy.rar, then open and your file is there.
b) Leave the file extension as is, right click, open with WinRar and your file is there
Speed Up Shutdown Time for WinXP
So if extreme security isn't required, then shut down XP without clearing your paging file by :-
1. Run the Registry Editor ( type regedit in Run and enter)
2. Go to: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
3. Change the value of ClearPageFileAtShutdown to 0.
4.Close the Registry and restart your computer.
Now on while turning off XP , the paging file won't be cleared, and shut down will be more quickly.
Thursday, September 11, 2008
Difference between JDK and JRE
Typically, each JDK contains one (or more) JRE's along with the various development tools like the Java source compilers, bundling and deployment tools, debuggers, development libraries, etc.
Tuesday, September 09, 2008
Determine when the web-page last updated
To find this date and time, type the following script in the Internet Explorer's address bar and press enter key.
javascript:alert(document.lastModified)
Friday, August 15, 2008
Move mouse cursor without touching mouse
You can move your mouse cursor with keyboard itself.
To activate this Press Alt + Shift + Numlock.
You will get a mouse keys dialog.
You can do the settings(Configure your mouse speed,etc) in this box and click Ok button.
Use number pad keys 1,2,3,4,5,6,7,8,9 to control the mouse cursor.
For example, pressing numberpad key 5 will do the left-click
Pressing the + key will do double click
Pressing insert key will hold the mouse cursor
Pressing delete key will release the mouse cursor
To deactivate moving mouse cursor using keyboard , just press numlock.
Tuesday, August 05, 2008
Uses of F4 key
1) Pressing F4 key will move the keyboard cursor to the address bar(Both in windows explorer and Internet explorer) and also drop down the address combo box.
2) Pressing Alt + F4 will close the application. If no application is opened, the shutdown dialog box will be opened.
3) Pressing Ctrl + F4 will close only the currently opened document in the application. (For example, if you have opened two pdf document in the acrobat reader, only the currently viewing pdf document will be closed and not the acrobat reader application).
Wednesday, July 30, 2008
Locate ATMs at ur location
To use this service, please click the link below.
http://visa.via.infonow.net/locator/global/
Monday, July 21, 2008
WORK INDEPENDENTLY WITHOUT MOUSE (RARE WINDOWS SHORT-CUTS)
To open the below programs, we can type the following commands in the run window.
Add or Remove Programs - appwiz.cpl
Add New Hardware - hdwwiz.cpl
Adjust date and time - timedate.cpl
Add environment variables - sysdm.cpl
Add fonts - fonts
Open Visual Studio.Net - devenv
Open Visual Studio - msdev
Open internet options - inetcpl.cpl
Open desktop properties - desk.cpl
Open paint - mspaint
Open MSWORD - winword
open MSEXCEL - EXCEL
open MSPOWERPOINT - POWERPNT
open MSACCESS - MSACCESS
open infopath - INFOPATH
Mouse properties - main.cpl
keyboard properties - main.cpl keyboard
User Accounts - nusrmgr.cpl
Internet explorer - iexplore
Windows explorer - explorer
Sounds and Audio devices - mmsys.cpl
Regional and Language options - intl.cpl
PowerOptions - powercfg.cpl
Phone and Modem options - telephon.cpl
Network Connections - ncpa.cpl
Accessibility Options - access.cpl
Saturday, July 12, 2008
Use Alt + D to go to address bar
Now try pressing ALT + D, the control will go to the address bar, and the link in the address bar get selected. So without moving mouse and then typing the new address, just we can type ALT + D and then type the new address.
Monday, July 07, 2008
Web Site Certificates
First of all, if a certain company or organization wants their Web site to use encryption and be secure, they must obtain a site (or host) certificate. If they don't, they will not be registered as a secure Web site. So, how do you tell if a site is secure or not? Well, we've gone over this before, but let's cover it one more time, just to be sure we're all on the same page. There are two things you can check on to find out if a site is secure or not. The first is a little yellow padlock in the bottom right corner of your Web browser. The padlock should be closed (locked) as well. The second is how the Web site's URL reads. On a secure site, the very beginning part will always be "https," rather than just "http." That extra "s" makes all the difference when it comes to security.
So, if you're visiting a site and you see either of those things, the site will have a certificate. You can view the certificate by double clicking the yellow padlock. Once you do that, a certificate dialogue box will pop up and you can read all about it. It will tell you the purpose of the certificate, who it's issued to, who it was issued by and when it expires. (If the site you're on just uses the "https" method, just double click in the area where the padlock usually sits. Doing that will bring up the same certificate box for you). For example, when you purchase something from online software store, the checkout page is secure. If you double click the padlock on that page, you will be able to see our certificate.
Another way you can view a site's certificate is through your browser's menu options. In Internet Explorer, go to File, Properties and then click on the Certificates button. The same dialogue box will then come up for you. In Firefox, go to Tools, Page Info and then click on the Security tab. You can then click on the View button to see that site's certificate. That may be an easier way for you to access the certificate information.
source: From internet.
Tuesday, June 17, 2008
Regular expression
There are three important parts to a regular expression. Anchors are used to specify the position of the pattern in relation to a line of text (like ^ indicates the character(after ^) should be at the beginning of string and $ indicates character(before $) should be at the end of string ). Character Sets match one or more characters in a single position like [a-z] means any single alphabet(lower case) and [0-9] any digit between 0 to 9 .
Modifiers specify how many times the previous character set is repeated like * represents zero or more times and ? means one or more times.
For example:^AD*B$ matches a string that starts with ‘A’ and ends with ‘B’ and should contain zero or more ‘D’s like AB, ADB, ADDB, ADDDB…..
Regular expressions are case sensitive.
There are some operators like:
\w - Matches a word character
\W - Matches a non word character
\s - Matches a space, a new line character or a tab
\d - Matches a digit character
References:
http://www.regular-expressions.info/tutorial.html http://www.grymoire.com/Unix/Regular.html http://www.2150.com/regexfilter/Documentation/regular_expressions.asp
Wednesday, June 11, 2008
Motherboard Cleaning Tips
- To clean your motherboard first unplugs your system power from the electrical outlet.
- Using the screwdriver remove the side covers of your computer case and put them to one side.
- Check all data and power cables connections. Inspect all motherboard PCI and AGP slots.
- Remove all add-on card of your motherboard for example RAM, modem, VGA, sound card and LAN card.
- Now blow the air around all the motherboard sides and keeping away your blower nozzle 4 to 5 inches away from main board components. You can use vacuum cleaner also for this purpose but compressed air is the better solution to clean a system.
- At the end assemble back all cards, cables and side covers of your system.
- I recommend you doing this after every three months if you want to save your system life.
Source: Gathered from Internet, while browsing through a Site.
Wednesday, April 30, 2008
Speed up your slow internet connection
This technique is more useful for static websites and for email applications but don't accelerate with secure and downloading audio or video files. Some good web accelerator retains your system cache to reuse websites with faster speed and can also block windows pop-up. If you are using FTP sites and downloading any program using dial-up, then web accelerator is not for you. There are various web accelerator software are free available on internet, visit and download it to enjoy your connection.
Wednesday, April 16, 2008
Wheel Mouse Tricks
Next time you visit a page like that, hold down your CTRL key and roll the wheel on your wheel mouse. You'll find that you can increase / decrease the font size as fast as your finger can spin that little wheel.
Wednesday, March 12, 2008
Windows Office shortcut keys
2 Alt O, T - FormatTabs : Brings up the Format Tabs dialog
3 Shift + F5 - GoBack : Returns to the previous insertion point (goes back to up to 3 points, then returns to where you started; this is one of the most useful shortcuts of them all. Also useful when opening a document, if you want to g straight to where you were last editing it)
4 Ctrl + > - GrowFont : Increases the font size of the selection
5 Ctrl + ] - GrowFontOnePoint : Increases the font size of the selection by one point
6 Ctrl + T (or drag the ruler) - HangingIndent : Increases the hanging indent
7 F1 - Help : Microsoft Word Help
8 Shift + F1 - HelpTool : Lets you get help on a command or screen region or examine text properties
9 Ctrl + Shift + H - Hidden : Makes the selection hidden text (toggle)
10 Alt O, P - FormatParagraph : Brings up the Format Paragraph dialog


